By Raul Bernardino
Introduction:
Nowadays, the network management has become very complex issues; this is starting from a single host to a millions hosts round the globe. We simple just don’t know who they are in the globe networks. Therefore, it is important to treat network management as an integral part of the network infrastructure management. Moreover, it is to enable us in monitoring and controlling the traffics. It is also enable us in maintaining all resources such as hardware, software, system configuration, and etc.
The Management Information Base (MIB) is virtual storage information of the objects that transmits through the networks. As per 2006, there were more than 200 standards of the MIB modules. The Internet Engineering Task Force (IETF) is a group of individuals that care about internet quality, influence designers, and manage the internet. They (IETF) adopted these standards and standardized this object identification with framework of the Open System Interconnection (OSI). The OSI object identifier tree can be sees in the diagram below:
Q1a: The ‘1.2.840.113549’ standards object identifier (OIDs) is for the RSADSI. Where the ‘1’ is for ISO assigned OIDs, ‘1.2’ is for ISO member body, ‘1.2.840’ is for USA, and ‘1.2.840.113549 is for RSADSI.
Q1b: The new Microsoft file format product in the OIDs tree is ‘1.2.840.113556.4.x’. Where ‘1’ is for ISO assigned OIDs, ‘1.2’ is for ISO member body, ‘1.2.840’ is for USA, and ‘1.2.840.113556 is for Microsoft, ‘1.2.840.113556.4’ is for Microsoft file format, and ‘1.2.840.113556.4.x’ is for new product of Microsoft file format.
The SNMP engine and application will be taking care of the differences
of the machine architecture, data format, message processing, and it is
including the security of data communication over the network. As it shows in diagram
below:
Introduction:
Nowadays, the network management has become very complex issues; this is starting from a single host to a millions hosts round the globe. We simple just don’t know who they are in the globe networks. Therefore, it is important to treat network management as an integral part of the network infrastructure management. Moreover, it is to enable us in monitoring and controlling the traffics. It is also enable us in maintaining all resources such as hardware, software, system configuration, and etc.
The Management Information Base (MIB) is virtual storage information of the objects that transmits through the networks. As per 2006, there were more than 200 standards of the MIB modules. The Internet Engineering Task Force (IETF) is a group of individuals that care about internet quality, influence designers, and manage the internet. They (IETF) adopted these standards and standardized this object identification with framework of the Open System Interconnection (OSI). The OSI object identifier tree can be sees in the diagram below:
Q1a: The ‘1.2.840.113549’ standards object identifier (OIDs) is for the RSADSI. Where the ‘1’ is for ISO assigned OIDs, ‘1.2’ is for ISO member body, ‘1.2.840’ is for USA, and ‘1.2.840.113549 is for RSADSI.
Q1b: The new Microsoft file format product in the OIDs tree is ‘1.2.840.113556.4.x’. Where ‘1’ is for ISO assigned OIDs, ‘1.2’ is for ISO member body, ‘1.2.840’ is for USA, and ‘1.2.840.113556 is for Microsoft, ‘1.2.840.113556.4’ is for Microsoft file format, and ‘1.2.840.113556.4.x’ is for new product of Microsoft file format.
Q2: The
SNMP stands for Simple Network Management Protocol. The message types and
functions over the SNMP protocol as it shows in the table below:
The big
differences of the trap and request respond messages in SNMP as follows:
-
The trap
message: the SNMP agent sent message to the SNMP manager and it is not
requiring any responds from the SNMP manager, and it is including sent inform
request and respond; as it shows in figure 1, 2 and diagram below:
Figure 1 Trap Sent to SNMP Manager
Successfully
Figure 2 Inform Request Sent to SNMP Manager
Successfully
However,
if it is unsuccessful during trap message sent, the SNMP agent does not know
the trap has reached the destination and the SNMP manager also does not receive
any inform request as it shows in figure 3 below:
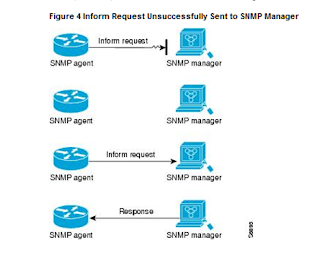
The agent sent several inform request from SNMP
agent to the SNMP manger on the trap model until it reaches the SNMP manger; as
it shows in figure 4 below:
-
While
the request and the response messages are sent by the agent to manager entity,
with the response coming back from the manager entity; as it shows in diagram
below:
Q3: The Internet has no presentation layer. Additionally, in the table
of the TCP/IP layer in which has four layers according to the IETF were defined
in RFC 1122:
We can compare the TCP/IP layer with 7 OSI layers as in diagram below:
The application layer in the TCP/IP is
representing application, presentation, and session layers in the OSI layer.
While internet layer in the TCP/IP represents network and data-link layer in
the 7 OSI layers. Other literatures especially bottom up approach split link
layer in to two layers such physical and data-link layer then TCP/IP layer
become five layers.
Moreover, network topology diagram below is illustrated two Internet host computers are
communicating through the local network boundaries comprised with the routers.
Q4: Before I am going to answer the question, I have to elaborate the
ASN.1. The ASN.1 stands for Abstract Syntax Notation 1 which is the ISO’s that
used numbers in the internet protocol, especially in the network management.
The question was how each of computers can read those transmitted data from
different architecture and program as it shows in diagram below:
The issue is on data formats and storage conventions. Potential
solutions as follows:
a)
The senders are learning format from the
receivers. In the real world analogy may
not apply. There is still pro and cons.
b)
The receivers are learning the sender’s
format. In the reality this can be a real world analogy however there is still
pro and cons.
c)
Senders and receivers are translate
independently each own format. It is not fitted with real world analogy.
In order to solve situation above:
1.
Translate local host format in to
independent host format
2.
Translate data in to independent host
format
3.
Translate independent host format to the
remote host format
The ASN.1 provides several things such as:
1.
In the ISO standard X.680 is used
extensively in the internet
2.
To define data type and object constructor
like SMI (Structure of Management Information)
3.
BER stands for Basic Encoding Rule in
which the ASN.1 will define data object to transmit. Where each transmission of
the object has a type, length, and value (TLV) encoding.
The TLV has tag value and type as follows:
Tag Value Type Description
1 BOOLEAN Value is true or false
2 INTEGER Can be arbitrary large
3 BITSTRING List of one or more bits
4 OCTET STRING List of one or more bytes
5 NULL No value
6 OBJECT IDENTFIER Name, in ASN.1 standard naming tree
9 REAL Floating point
Example of the BER in the TLV encoding for character string “Smith” with
value 259 as it can be illustrated in a diagram below:
The answer for strings “greg” and value 277. The binary for the decimal of 277 is 00000001 00010101. The first binary value is 1 and followed by value of the byte is 21. The first byte of the stream value is 4 in which indicating type of data is OCTET STRING and the length of OCTET STRING is 4 (“greg”); followed by 2 integers (type of data and length of integer). The result is ” 4 4 ‘g’ ‘r’ ‘e’ ‘g’ 2 2 1 21”, as it can be illustrated in a diagram below:
The answer for strings “greg” and value 277. The binary for the decimal of 277 is 00000001 00010101. The first binary value is 1 and followed by value of the byte is 21. The first byte of the stream value is 4 in which indicating type of data is OCTET STRING and the length of OCTET STRING is 4 (“greg”); followed by 2 integers (type of data and length of integer). The result is ” 4 4 ‘g’ ‘r’ ‘e’ ‘g’ 2 2 1 21”, as it can be illustrated in a diagram below:
Reference List:
1. Kurose, J.F. & Ross, K.W. (2010) Computer Networking: A Top-Down Approach.
5th ed. Boston:
Addison Wesley
2. University
of Liverpool/Laureate Online Education (2011) Lecture notes from Computer
Networking Module Seminar8 [Online]. Available from: University of
Liverpool/Laureate Online Education VLE (Accessed: 21 September 2011).
3. Cisco
IOS Software Releases 11.3: SNMP Inform Requests, [Online]. Available from: http://www.cisco.com/en/US/docs/ios/11_3/feature/guide/snmpinfm.html
(Accessed: 27 September 2011)
4. The deference between TCP/IP and OSI layer, [Online]. Available from: http://forums.techarena.in/technology-internet/1113879.htm
(Accessed: 27 September 2011)
5. Network Management Review question, [Online]. Available from: http://subjects.ee.unsw.edu.au/tele4354/downloads/revCh9.pdf
(Accessed: 27 September 2011)
6. RSA data security Inc, [Online]. Available from: http://www.alvestrand.no/objectid/1.2.840.113549.html
(Accessed: 27 September 2011)
7. Wikipedia (N), OSI model, [Online]. Available from: http://en.wikipedia.org/wiki/OSI_model
(Accessed:
30 September 2013)
8. Website (N), The
internet engineering Task Force, [Online].
Available from: http://www.ietf.org/(Accessed:
30 September 2013)
9. Wikipedia (N), Protocol Data Unit, [Online]. Available from: http://en.wikipedia.org/wiki/Protocol_data_unit
(Accessed:
30 September 2013)

















No comments:
Post a Comment